Client Side Encryption
Client Side Encryption
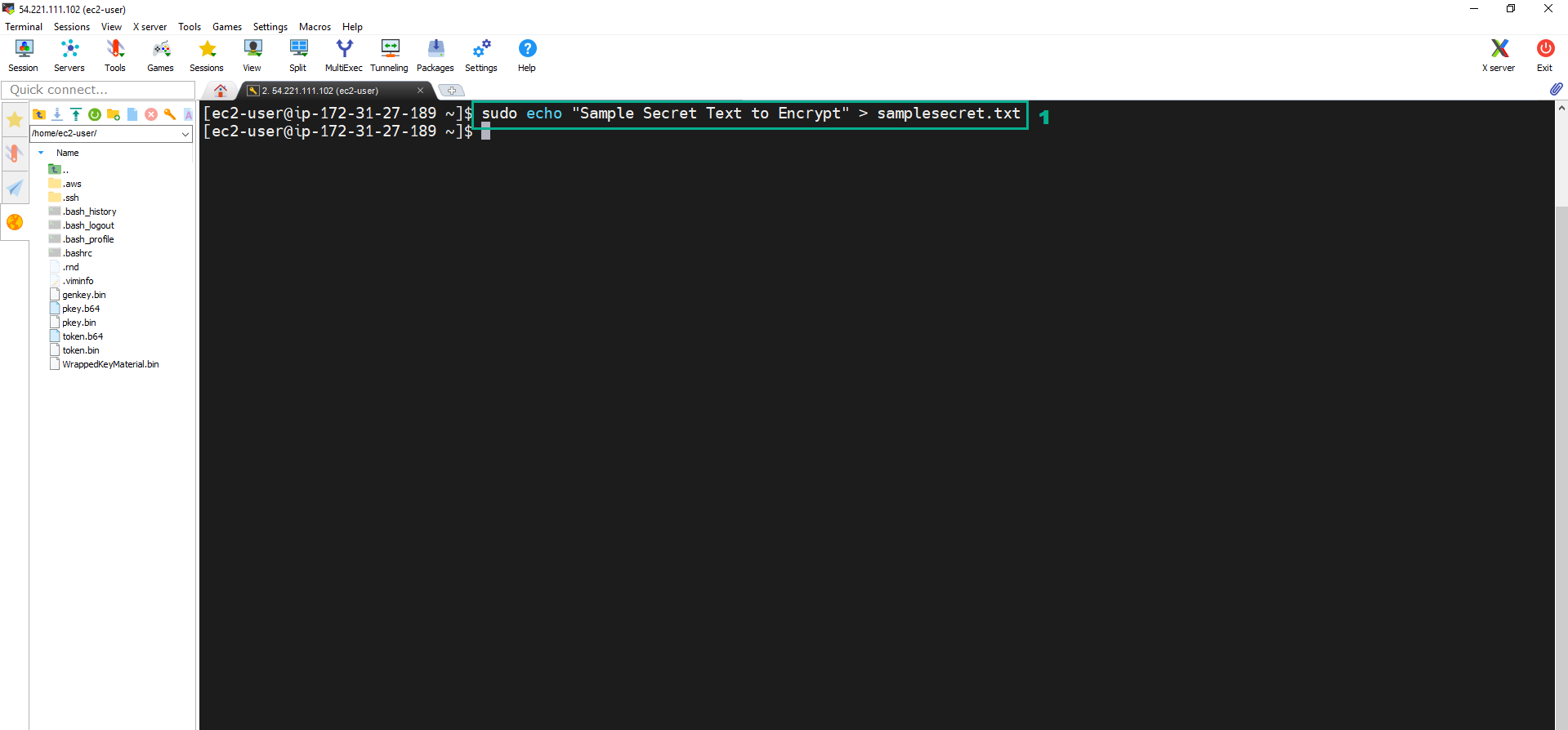
- Execute the below command to create the text file
sudo echo "Sample Secret Text to Encrypt" > samplesecret.txt
 2. Assign the permission to the Instance to create the key
2. Assign the permission to the Instance to create the key
- Go to AWS IAM Console.
- Click Policies.
- Click Create Policy.
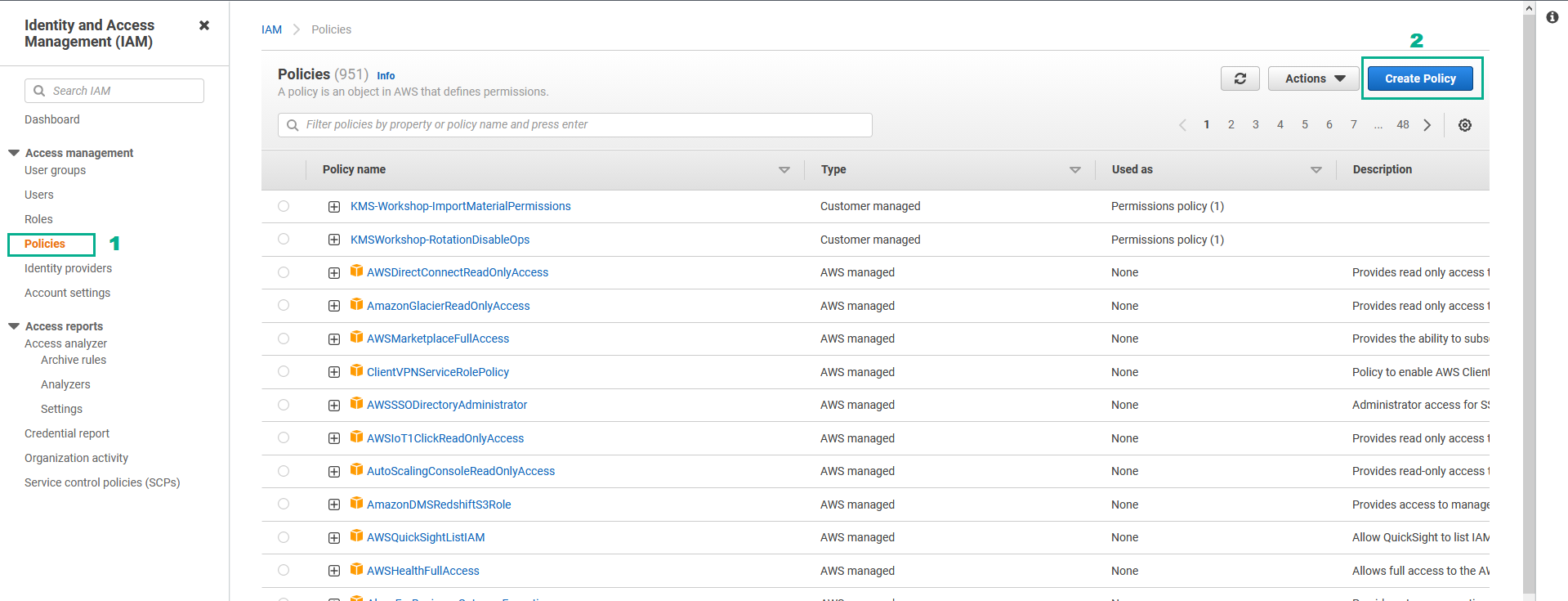
- AWS IAM Console Create policy page
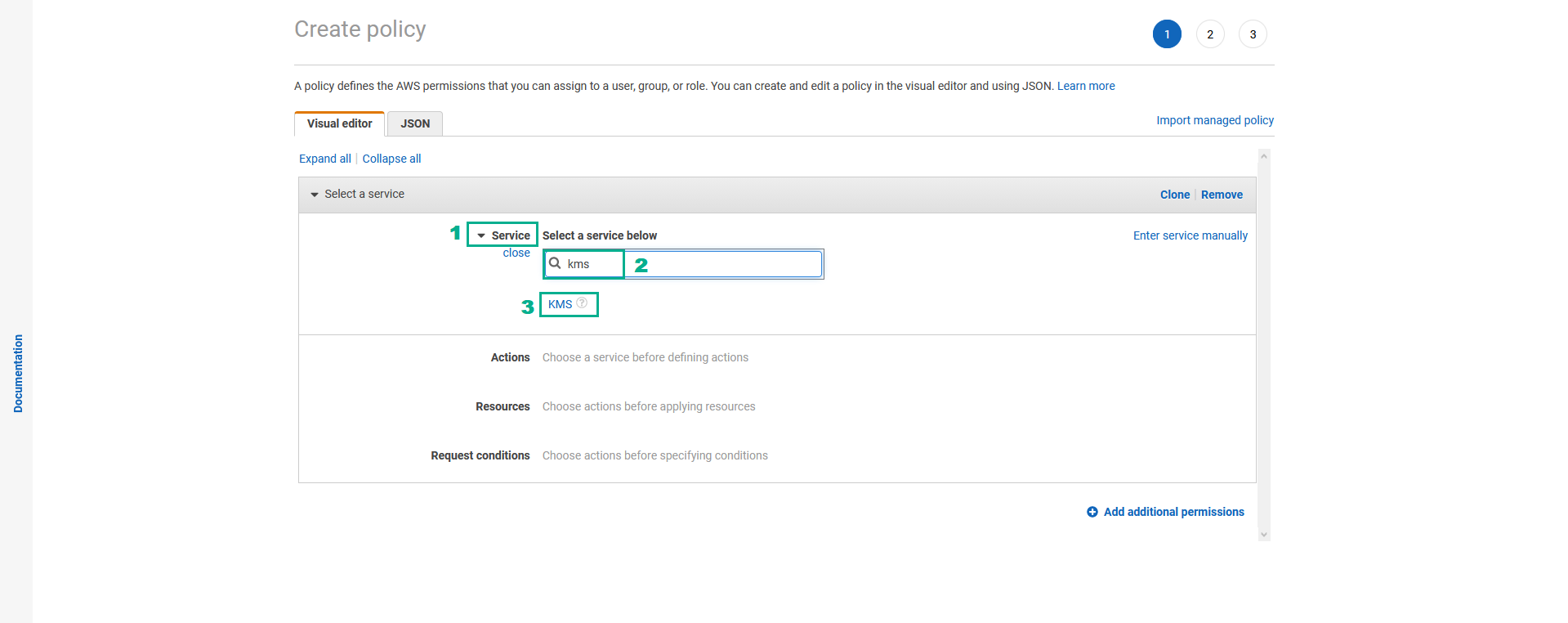
- Click Service.
- Type
kmsinto the search bar. - Click KMS
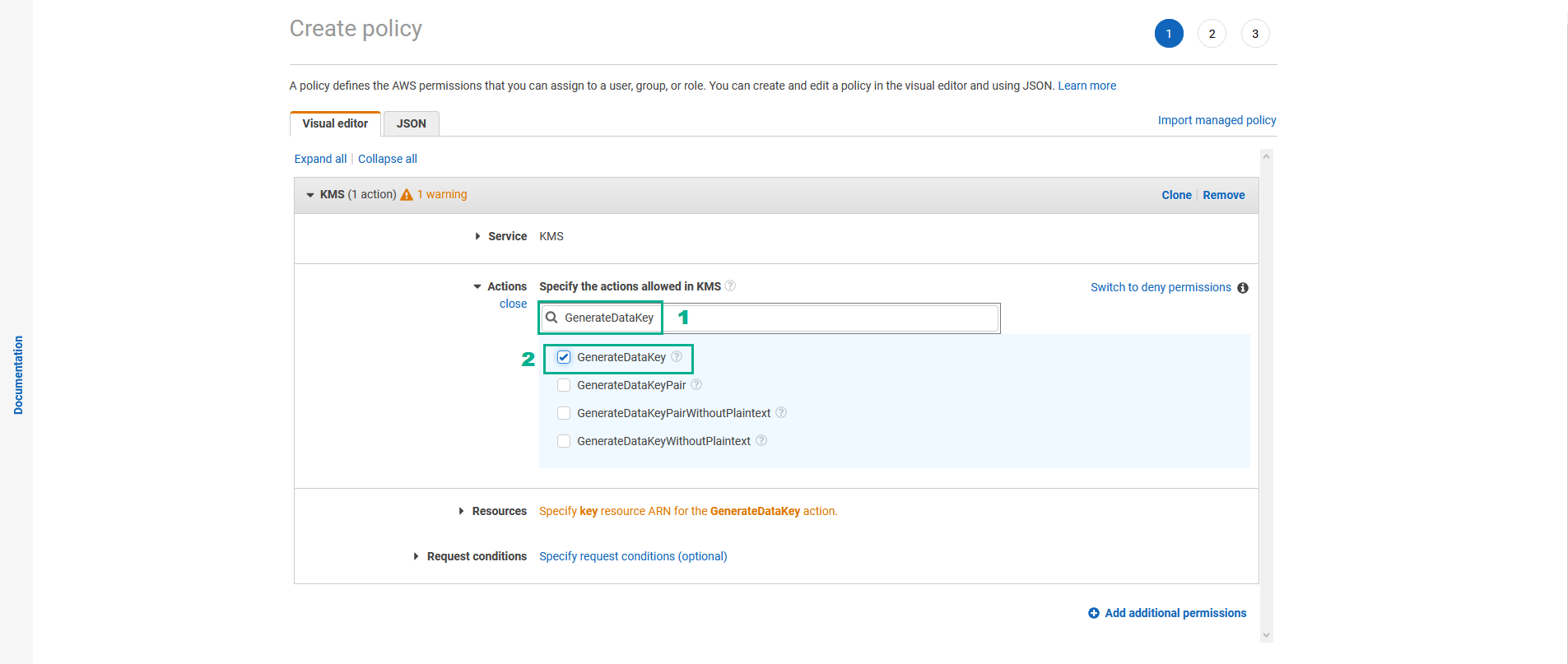
- In the Actions section
- Assign GenerateDataKey permission
- Type
GenerateDataKeyinto the search bar - Select GenerateDataKey
- Type
- Do the same for Encrypt permission, Decrypt permission, TagResource permission, Untagresource permission và GenerateDataKeyWithoutPlainText permission
- In the Resources section
- Click Resources
- Select Specific
- in the key section, Select Any in this account
- Click Next:Tags
- AWS IAM Console Add tags page
- Click Next:Review
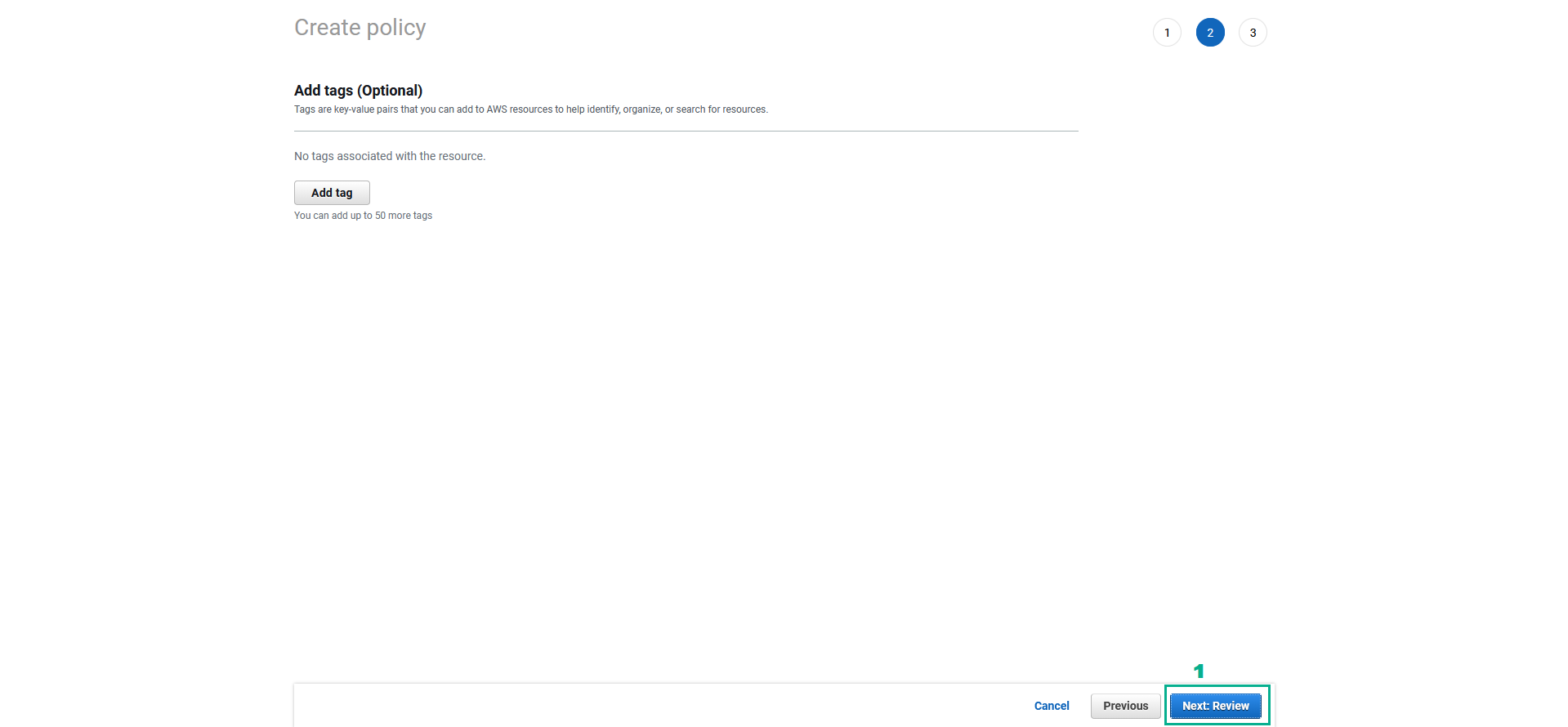
- AWS IAM Console Review policy page
- in the Name section, type
KMSWorkshop-AdditionalPermissions - Click Create Policy
- Attach KMSWorkshop-AdditionalPermissions policy to KMSWorkshop-InstanceInitRole role
- Go to AWS IAM Console.
- Click Roles.
- Click KMSWorkshop-InstanceInitRole.
- In the Permissions policies section
- Click Add permissions.
- Click Attach policies.
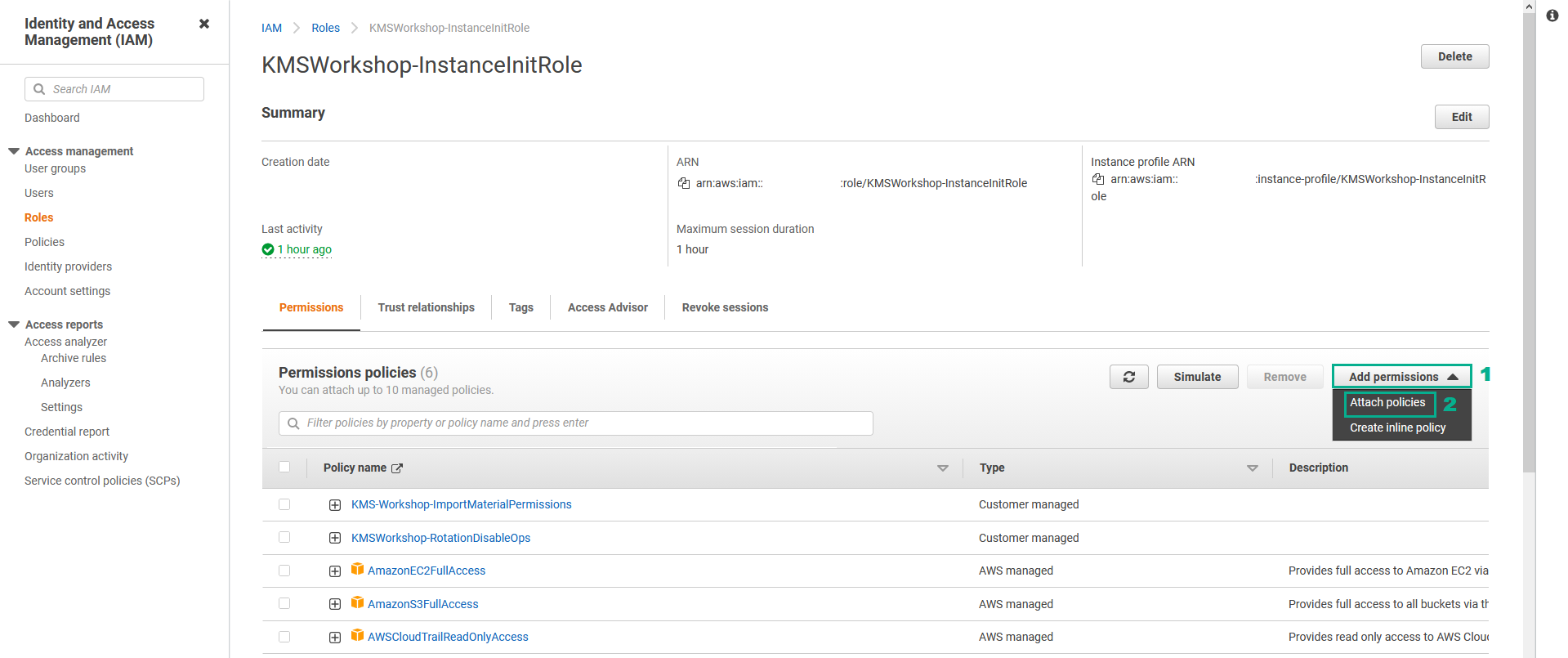
- In the Other permissions policies section
- Type
KMSWorkshop-AdditionalPermissionsinto the search bar, press Enter - Select KMSWorkshop-AdditionalPermissions.
- Click Attach policies.
- Execute the below command to create the Data key
aws kms generate-data-key --key-id alias/ImportedCMK --key-spec AES_256 --encryption-context project=workshop
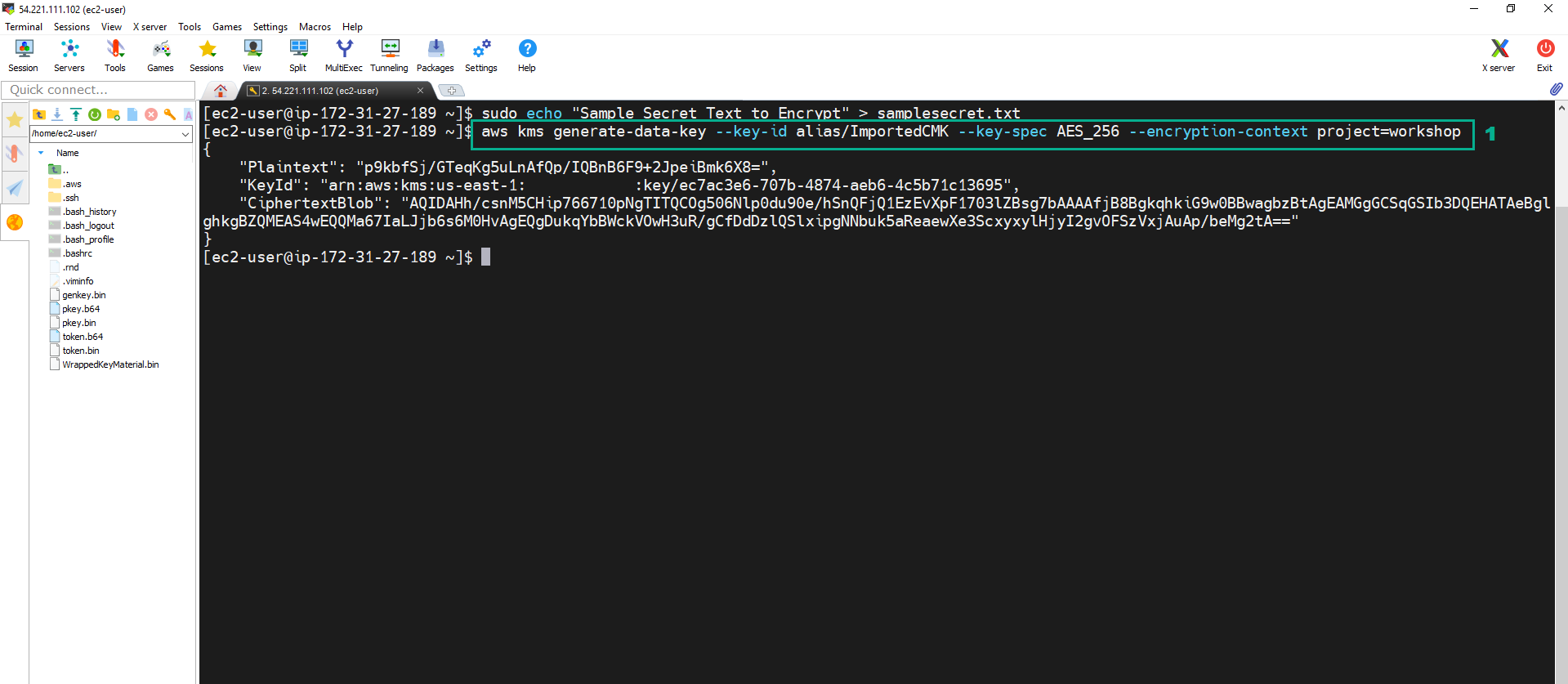
- The command will return a JSON output with:
- the plaintext data key - Plaintext key in b64 encoding
- the KeyId used to encrypt plaintext data key
- A CiphertextBlob which is the encrypted data key generated, in base64 enconding.
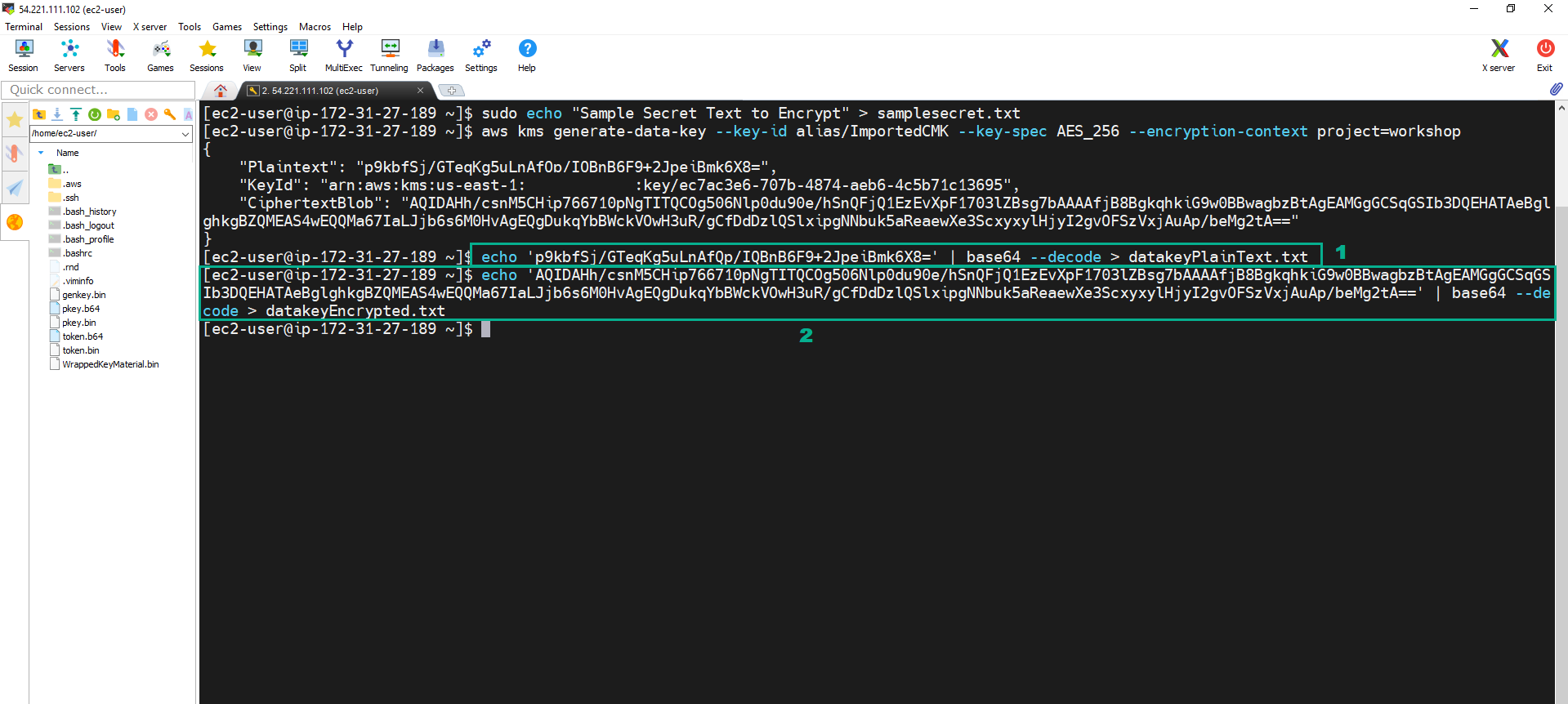
- Execute the below command to decode the Plaintext key and the CiphertextBlob we obtained above, as they are in b64, and store them in datakeyPlainText.txt file and datakeyEncrypted.txt file
echo '<Plantext value of the JSON file in step 11>' | base64 --decode > datakeyPlainText.txt
echo '<CipherTextBlob value of the JSON file in step 11>' | base64 --decode > datakeyEncrypted.txt
 13. Execute the below command to encrypt file samplesecret.txt in AES256 bits and saves the encrypted output to file “encryptedSecret.txt”.
13. Execute the below command to encrypt file samplesecret.txt in AES256 bits and saves the encrypted output to file “encryptedSecret.txt”.
openssl enc -e -aes256 -in samplesecret.txt -out encryptedSecret.txt -k fileb://datakeyPlainText.txt
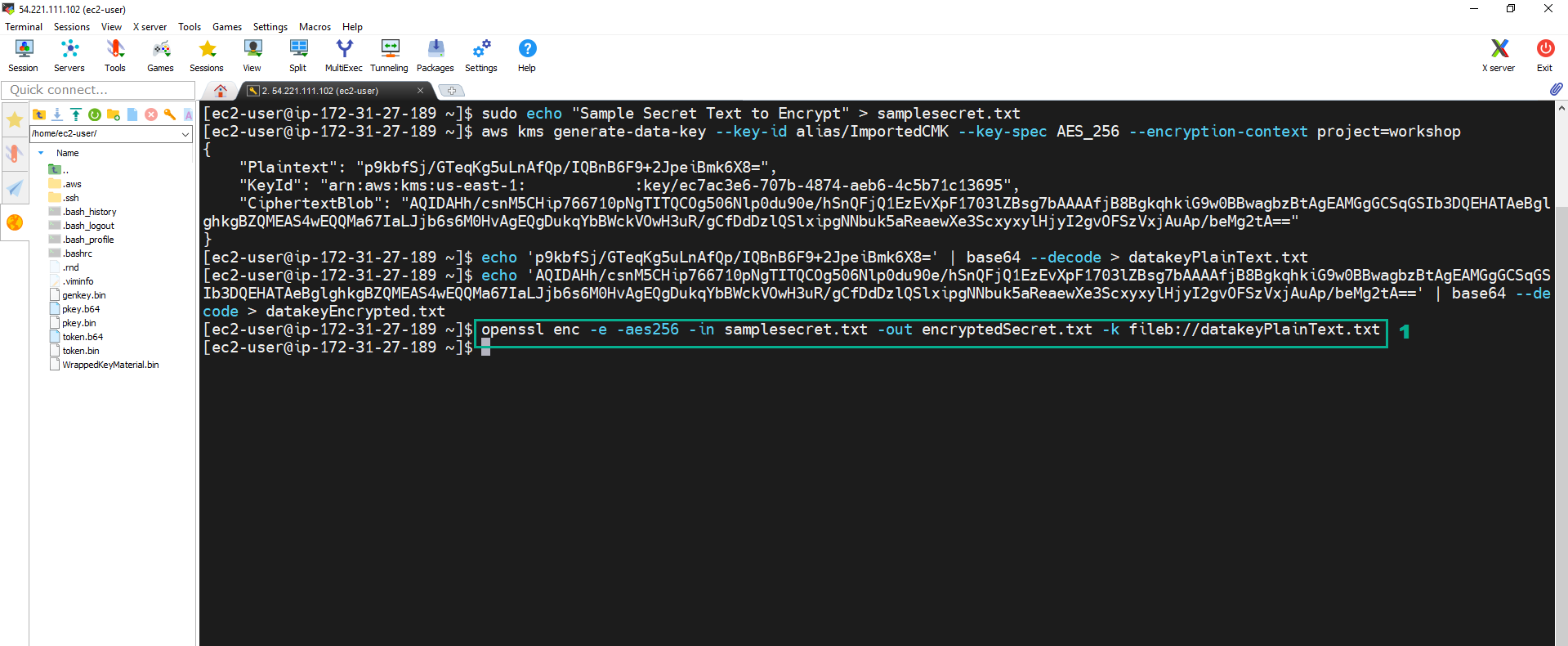 14. Execute the below command to check the encrypted content
14. Execute the below command to check the encrypted content
openssl enc -e -aes256 -in samplesecret.txt -out encryptedSecret.txt -k fileb://datakeyPlainText.txt
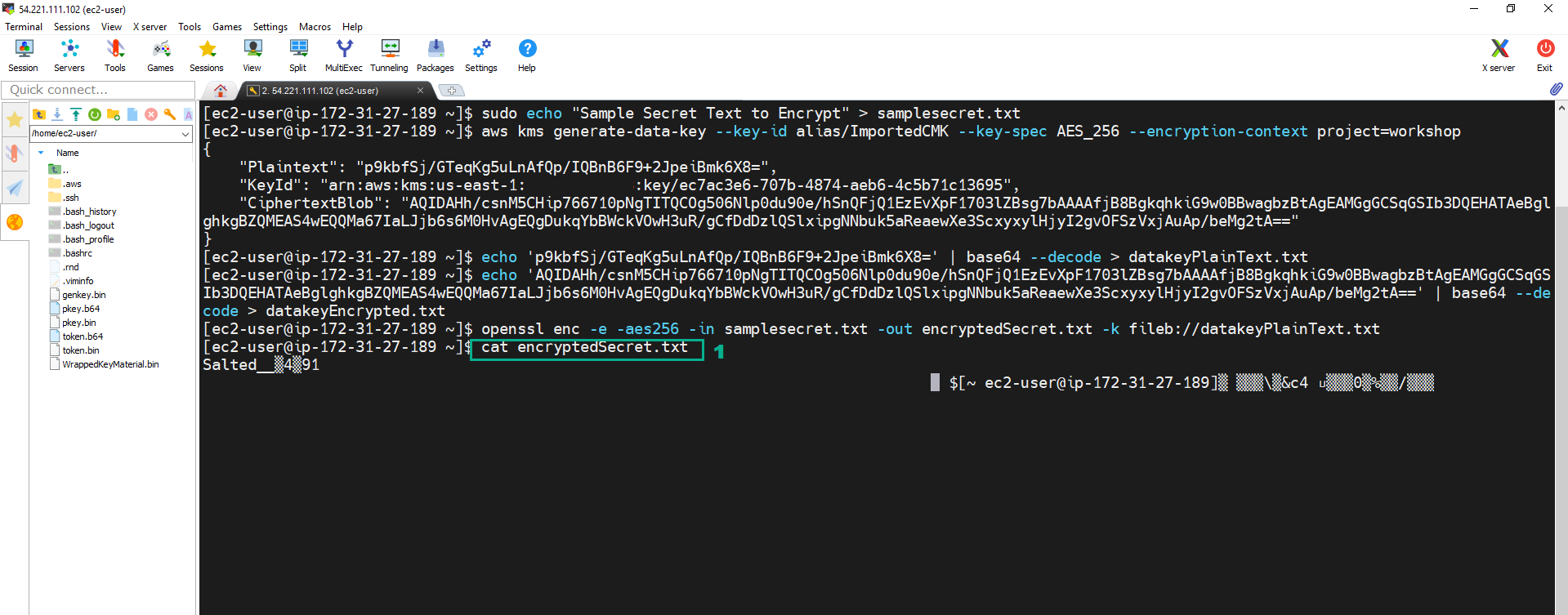 15. Execute the below command to delete the plaintext key.
15. Execute the below command to delete the plaintext key.
rm datakeyPlainText.txt
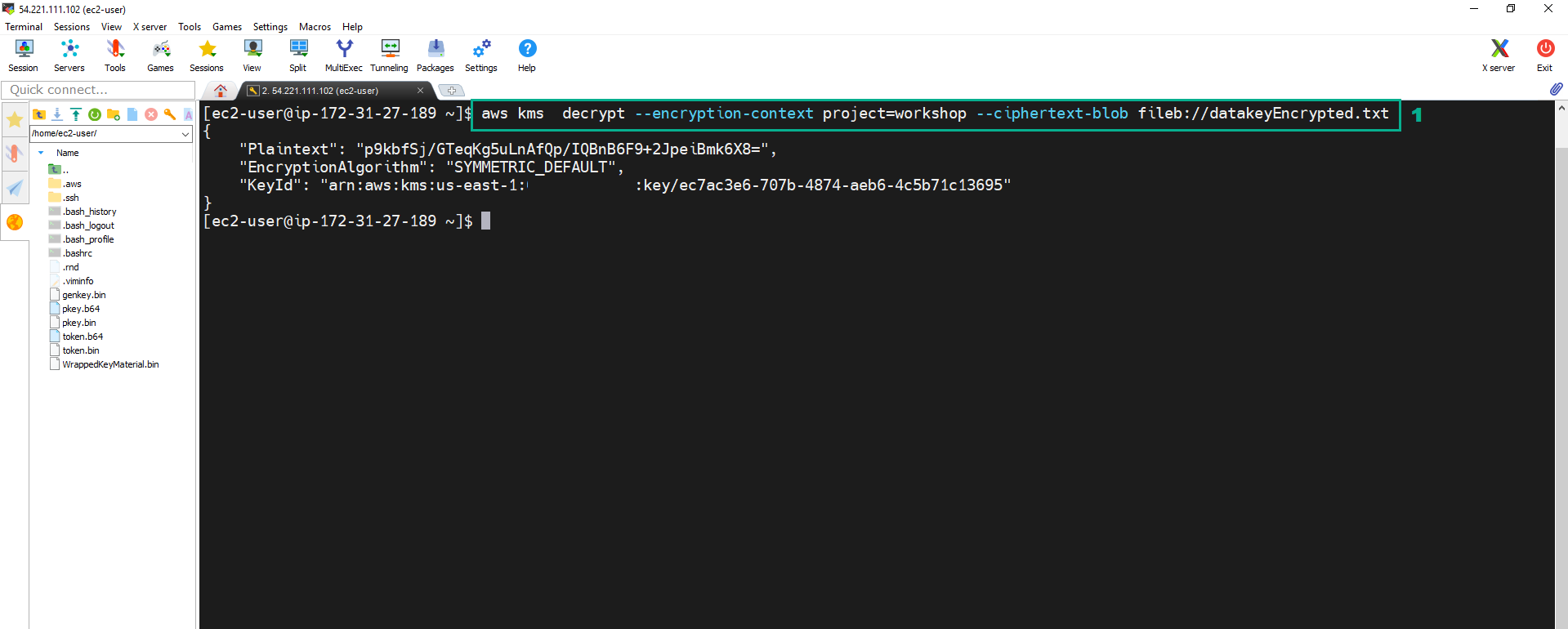
Following security best practice, we must to delete the Data Key in Plain Text after ecrypting the data. Therefore, we need dencrypt the encrypted data key to dencrypt the encrypted text file.
aws kms decrypt --encryption-context project=workshop --ciphertext-blob fileb://datakeyEncrypted.txt
 17. Execute the below command to decode the data key from base64 and use it to decrypt the encrypted secret file encryptedSecret.txt.
17. Execute the below command to decode the data key from base64 and use it to decrypt the encrypted secret file encryptedSecret.txt.
echo '<Plantext value of the JSON file in step 16>' | base64 --decode > datakeyPlainText.txt
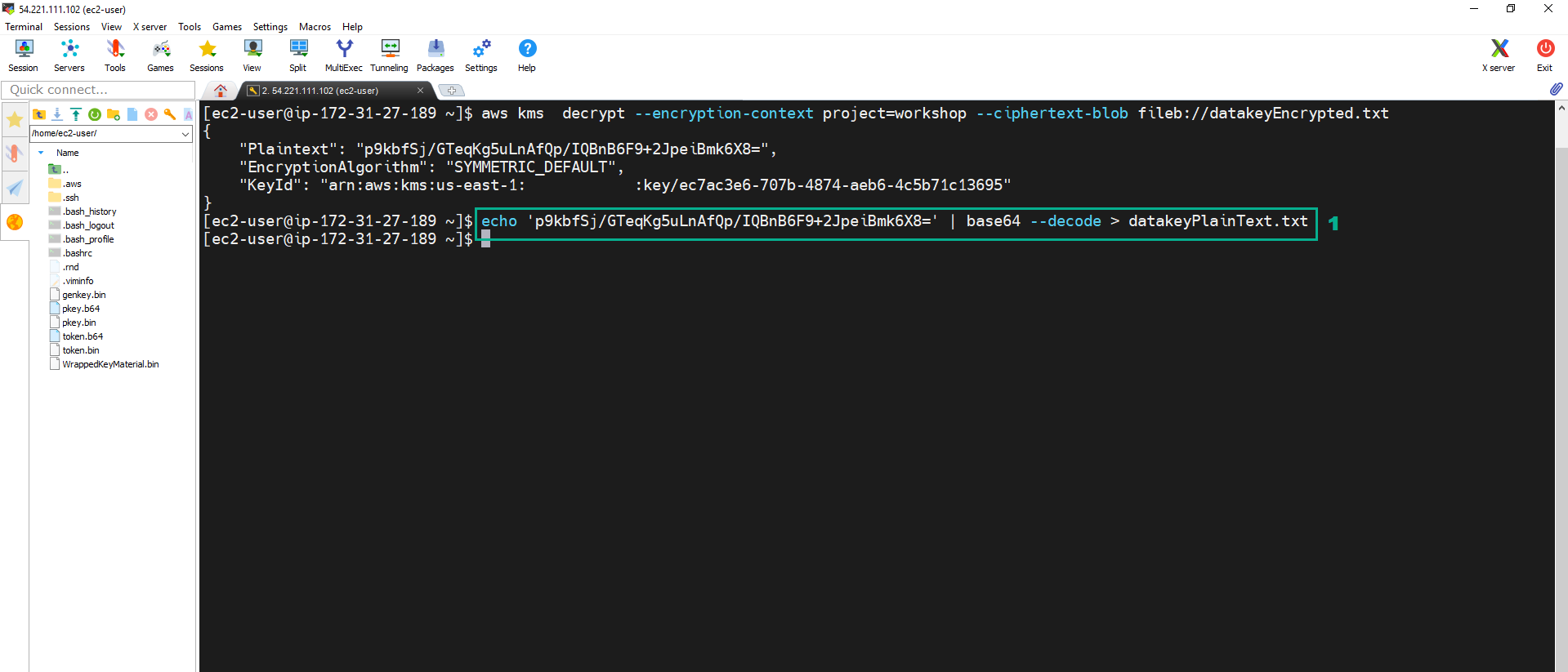 18. Execute the below command to decrypt ecrypted file Text
18. Execute the below command to decrypt ecrypted file Text
openssl enc -d -aes256 -in encryptedSecret.txt -k fileb://datakeyPlainText.txt
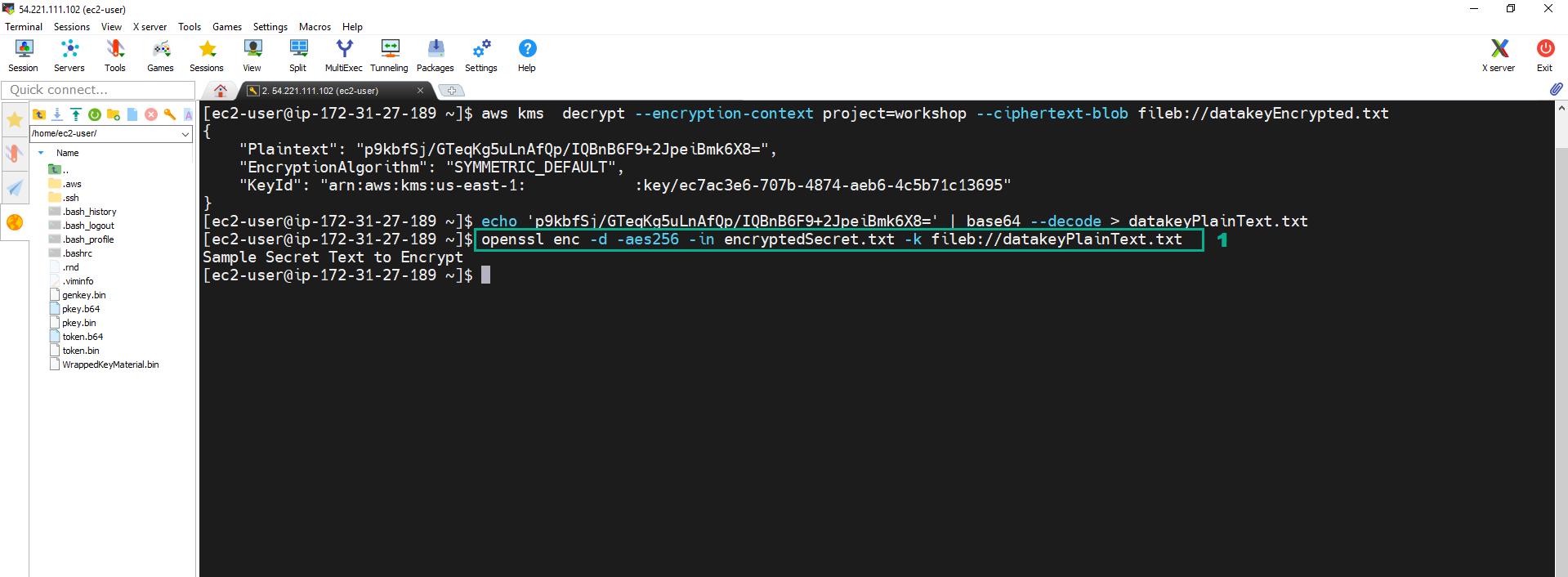 19. Execute the below command to delete the plaintext key.
19. Execute the below command to delete the plaintext key.
rm datakeyPlainText.txt
