Generate CMKs with your own key material
Generate CMKs with your own key material
- Execute the command:
aws kms create-key --origin=EXTERNAL
aws create-key command has –origin=EXTERNAL option, that indicates the key material will not come from AWS KMS, but from an external source.

- We created the CMK but we need note some fields:
- Enabled fields shows False instead of True.
- Key state fields shows PendingImport instead of Enabled.
Download Public key and import token from AWS KMS
- Execute the command:
aws kms get-parameters-for-import --key-id <key ID of your External CMK> --wrapping-algorithm RSAES_OAEP_SHA_1 --wrapping-key-spec RSA_2048
- The result is a JSON file with the public key base64 encoded, key id and import token base64 encoded.
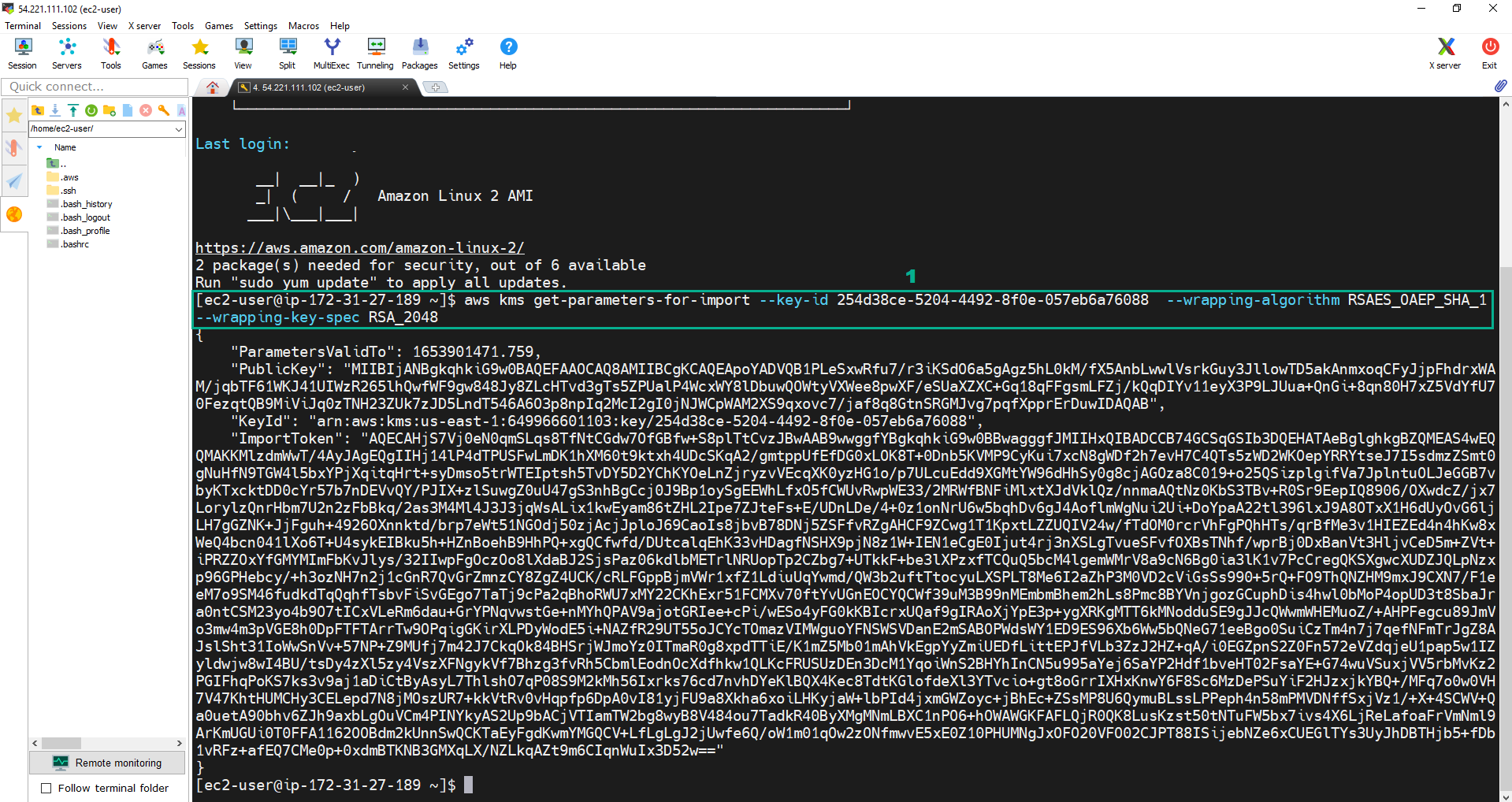
- Copy the PublicKey into pkey.b64 file.
- Copy the PublicKey.
- Execute the command:
vi pkey.b64.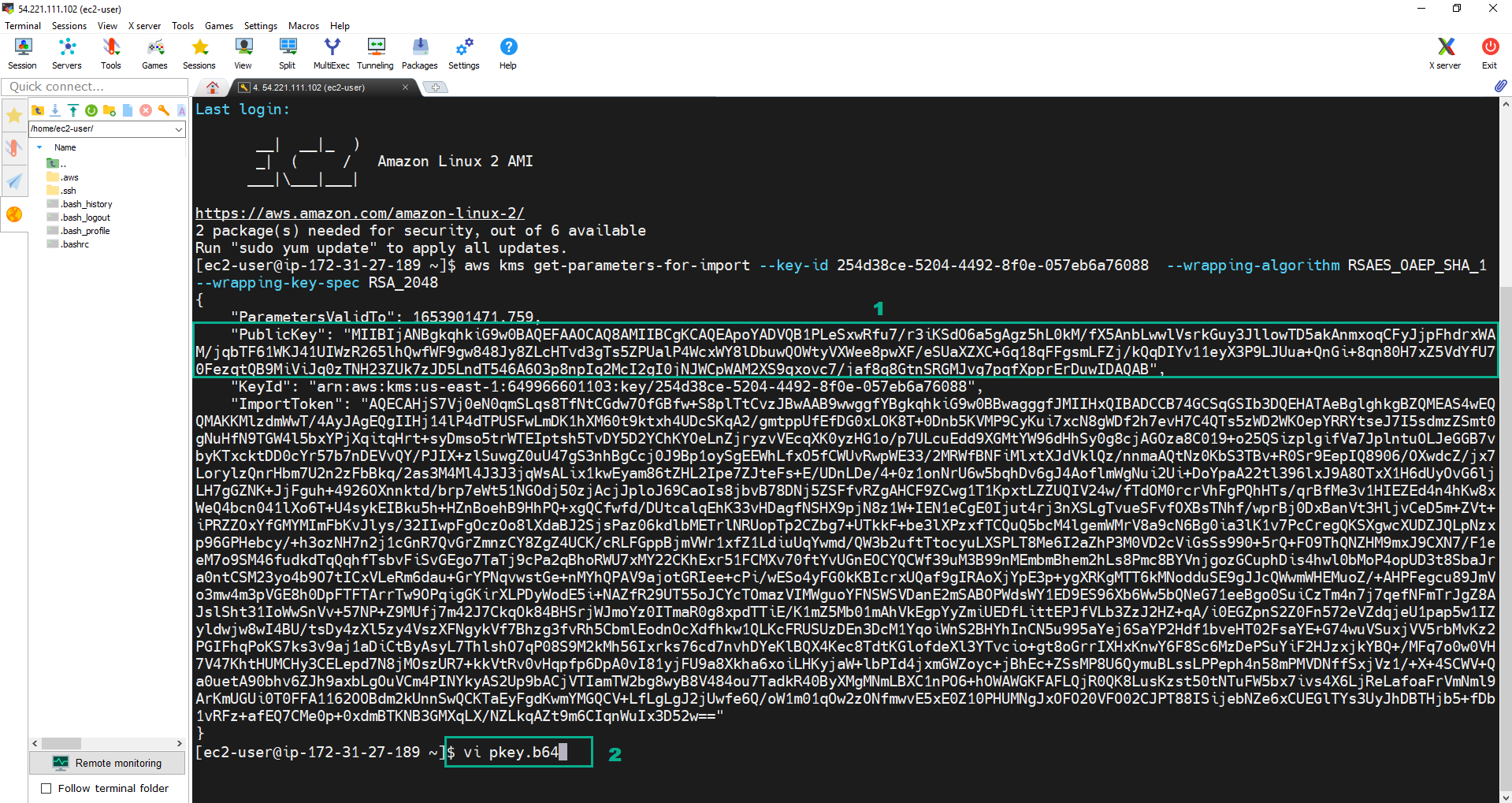
- Press i to change to the Insert mode. Paste the PublicKey we copied.
- Press Esc. Type
:wq. Press Enter to save file and quit.
- Do the same as the step 2 to copy the ImportToken into token.b64.
- Execute the command:
ls -lrtto check. We wil see pkey.b64 file and token.b64 file.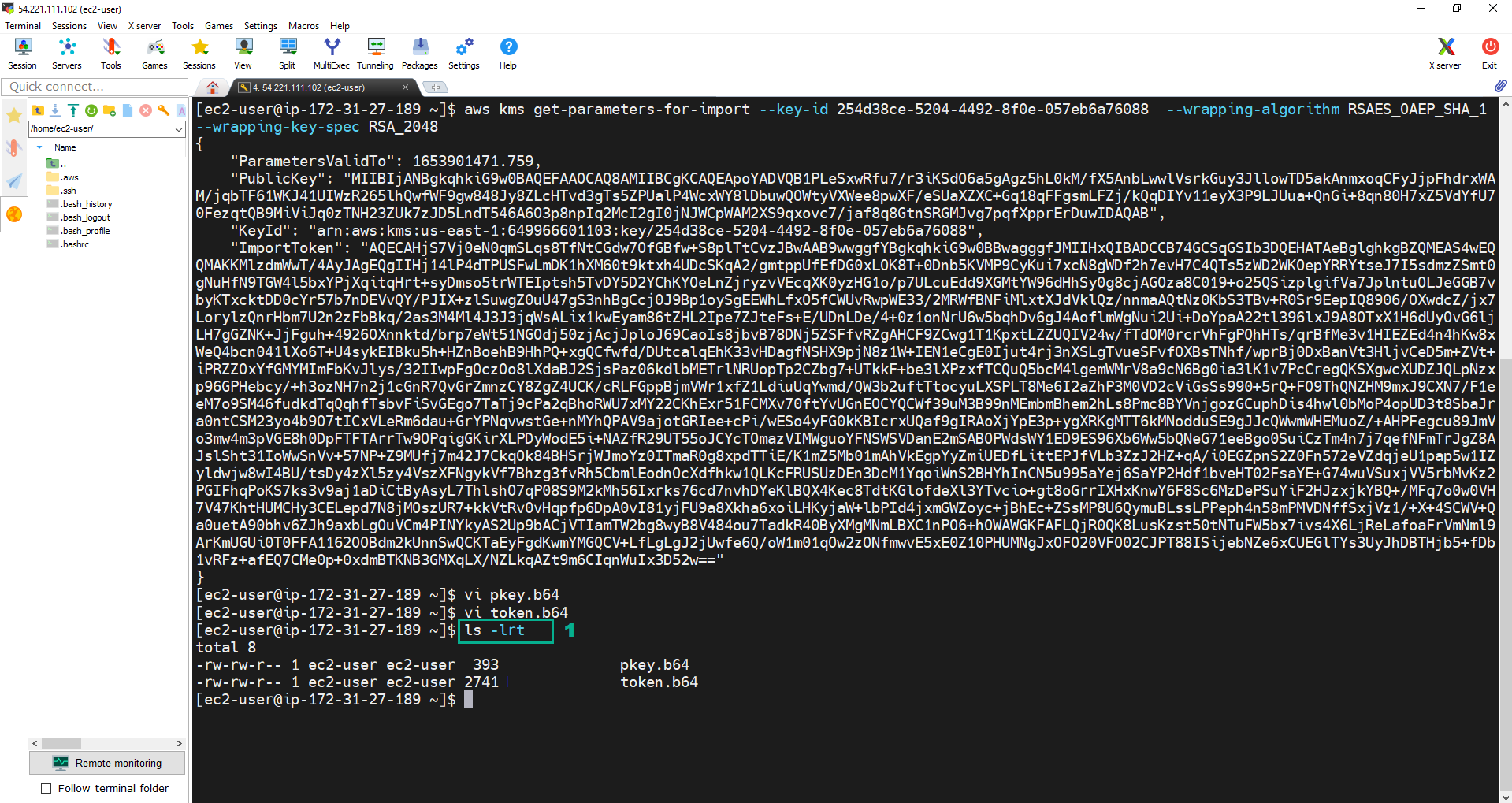
- Use OpenSSL to decode to convert the b64 files into binary files are pkey.bin anf token.bin
- Execute the command:
openssl enc -d -base64 -A -in pkey.b64 -out pkey.bin. - Execute the command:
openssl enc -d -base64 -A -in token.b64 -out token.bin. - Execute the command:
ls -lrtto check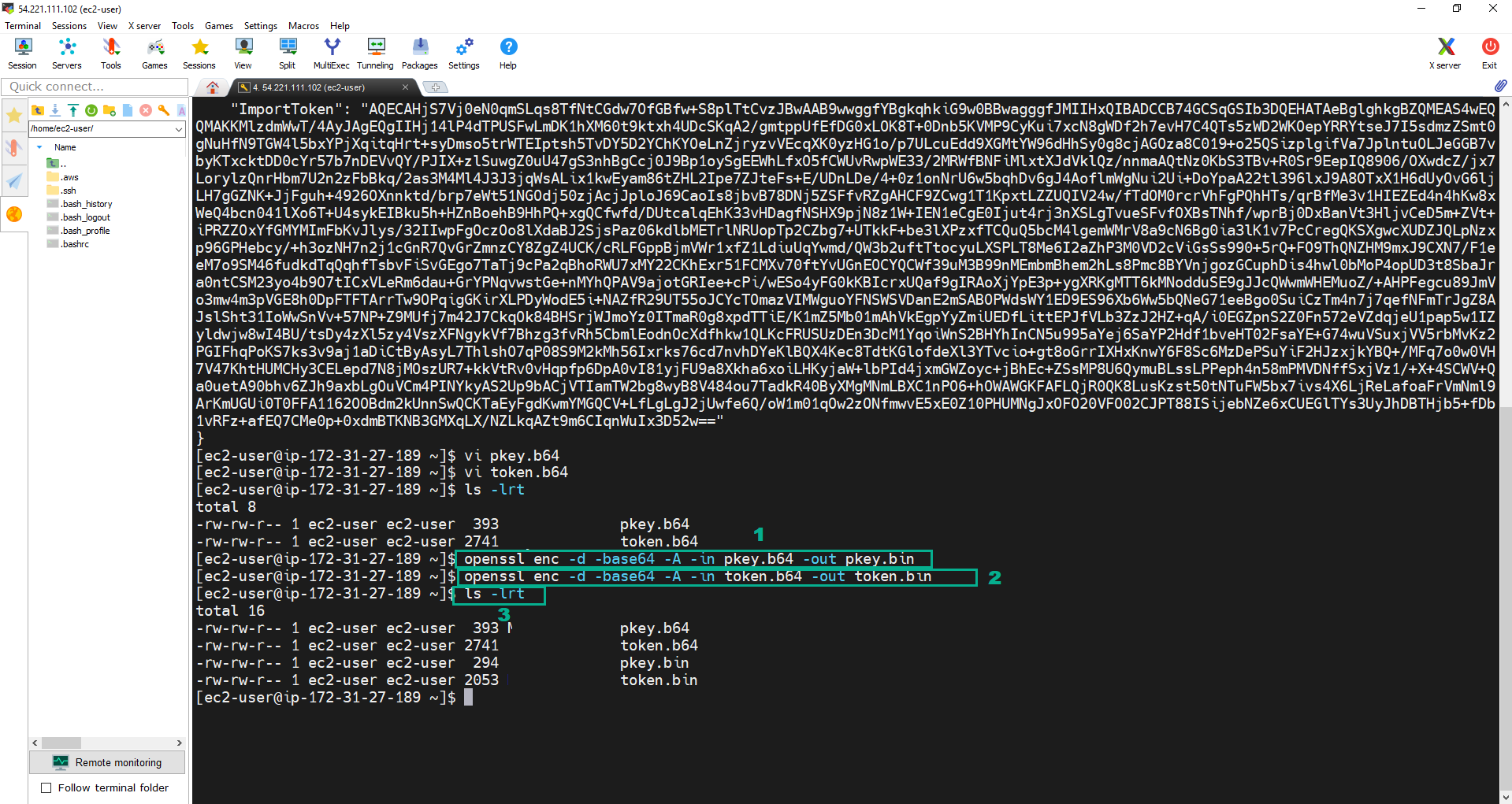
Create the import material and encrypt it for the import
Usually key material will come from an enterprise HSM or other key management system in the company that would be in charge of generating the keys. For the workshop, we will generate the keys with the OpenSSL library directly in our instance.
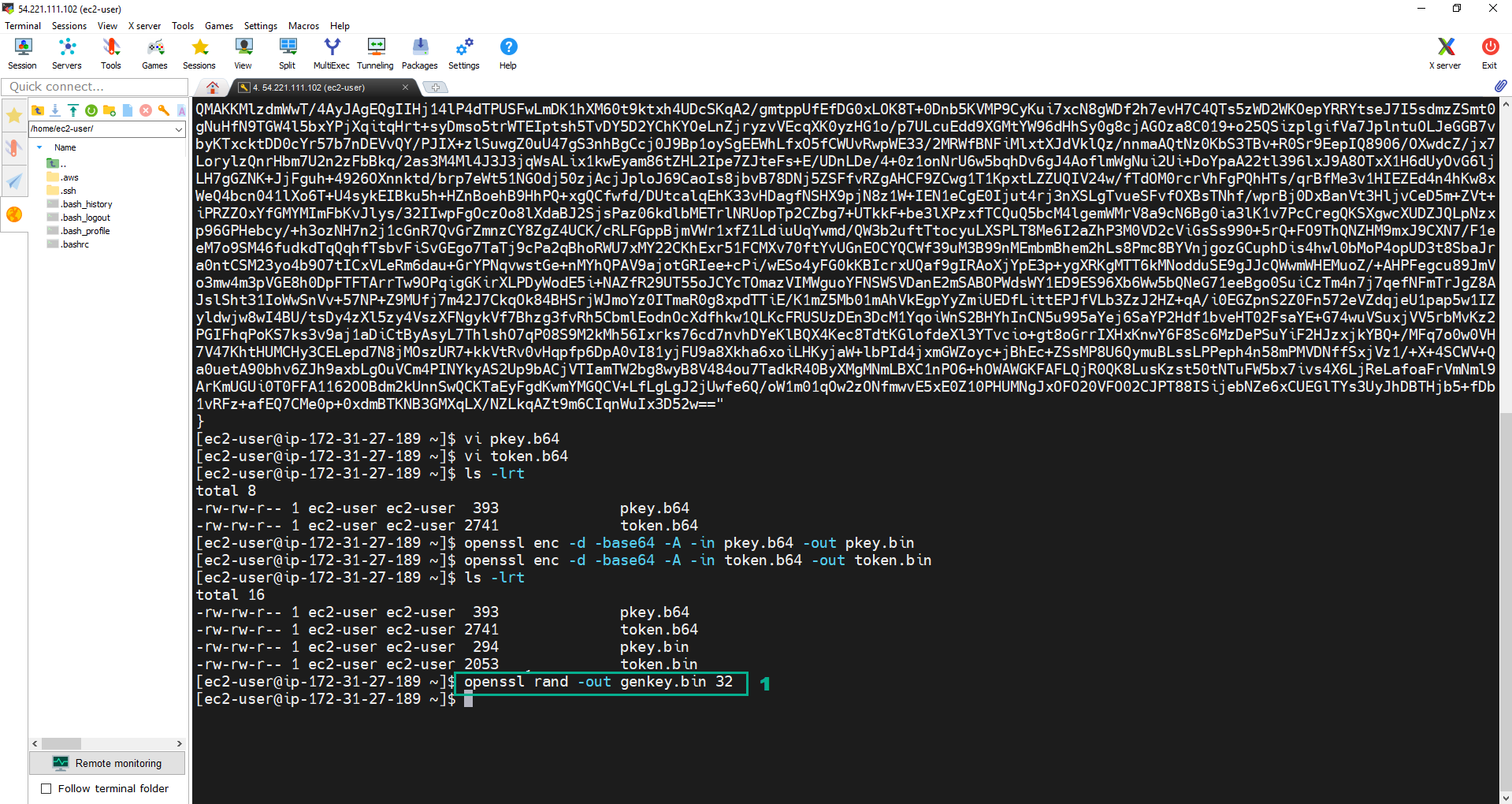
- Execute the below command to generate a 256 bit symmetric key and stores into file genkey.bin. The key that the file contains is our key material for the CMK.
openssl rand -out genkey.bin 32
 2. Encrypt the Key material. Then, saves the output in another file named WrappedKeyMaterial.bin.
2. Encrypt the Key material. Then, saves the output in another file named WrappedKeyMaterial.bin.
- Execute the command:
openssl rsautl -encrypt -in genkey.bin -oaep -inkey pkey.bin -keyform DER -pubin -out WrappedKeyMaterial.bin. - Execute the command:
ls -lrtto check.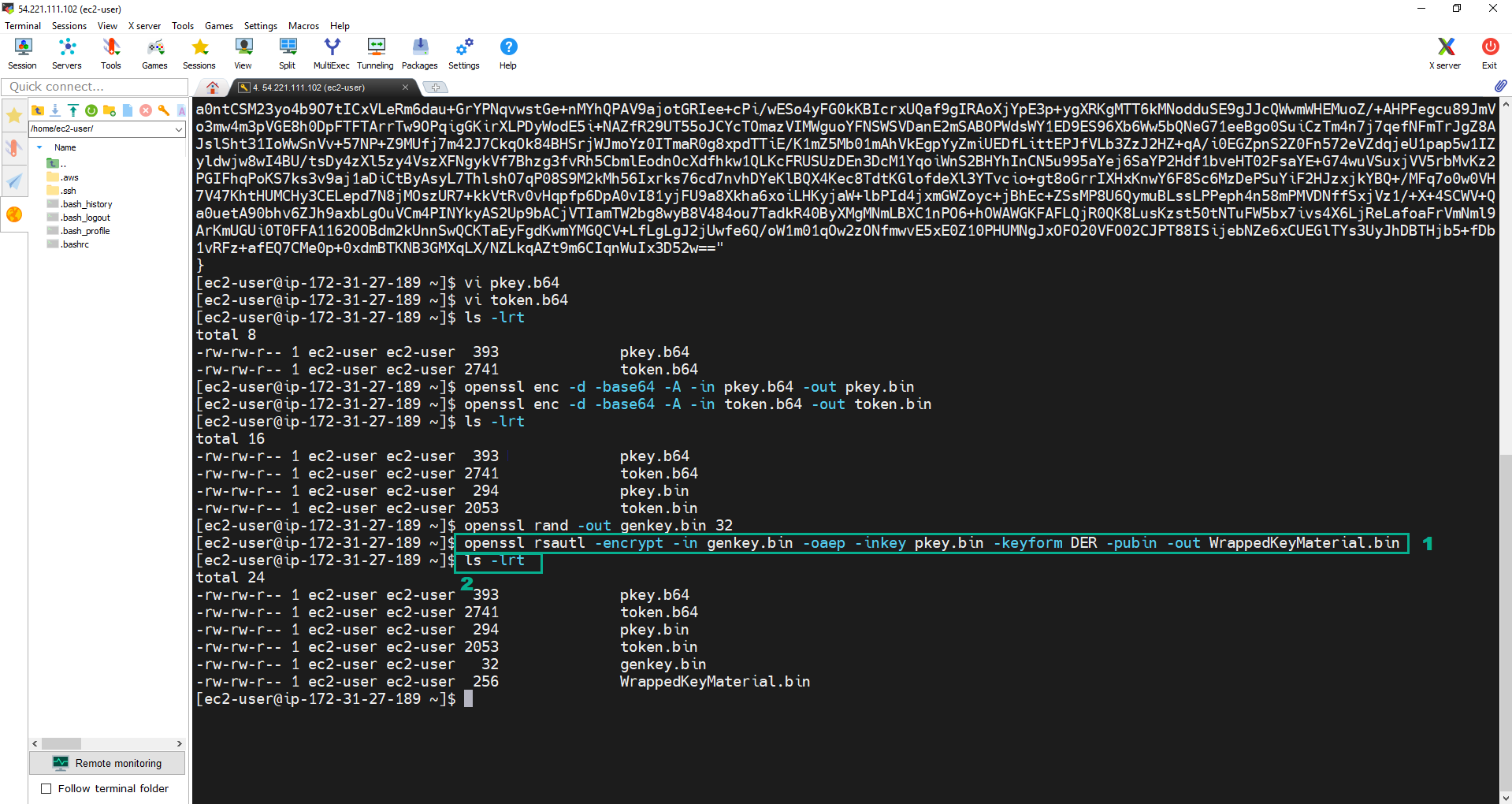
Import Key material
- Execute the command:
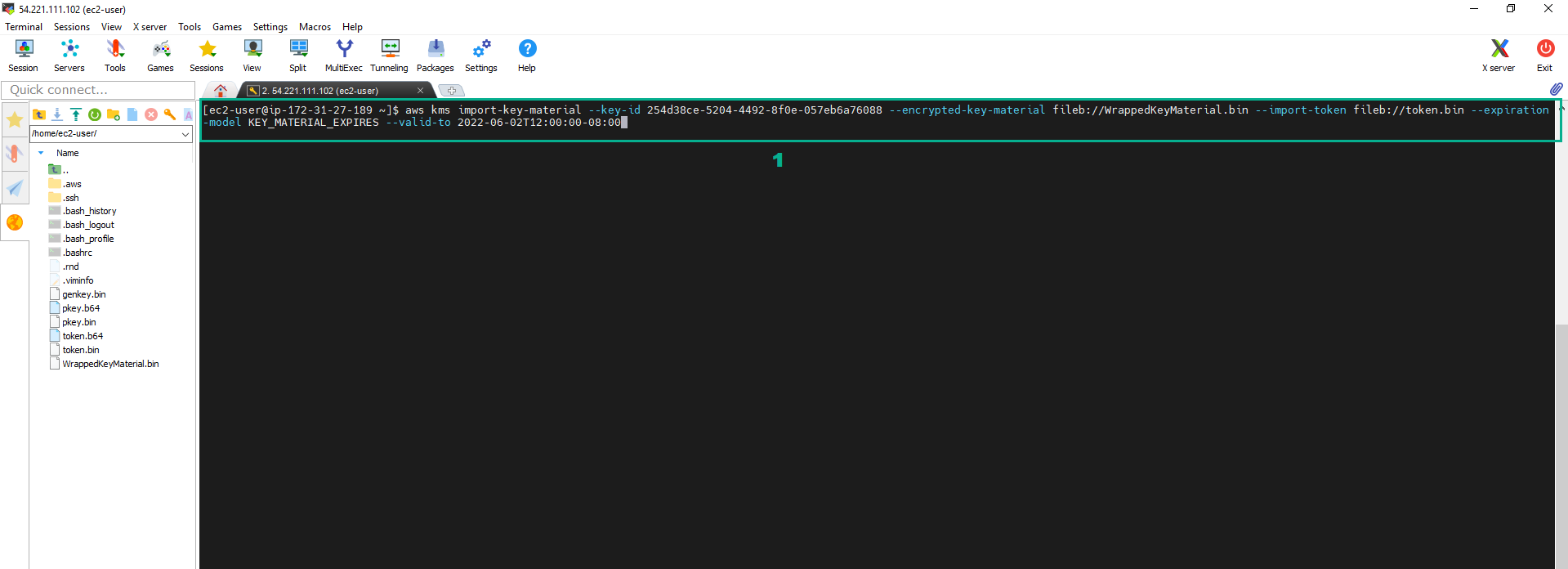
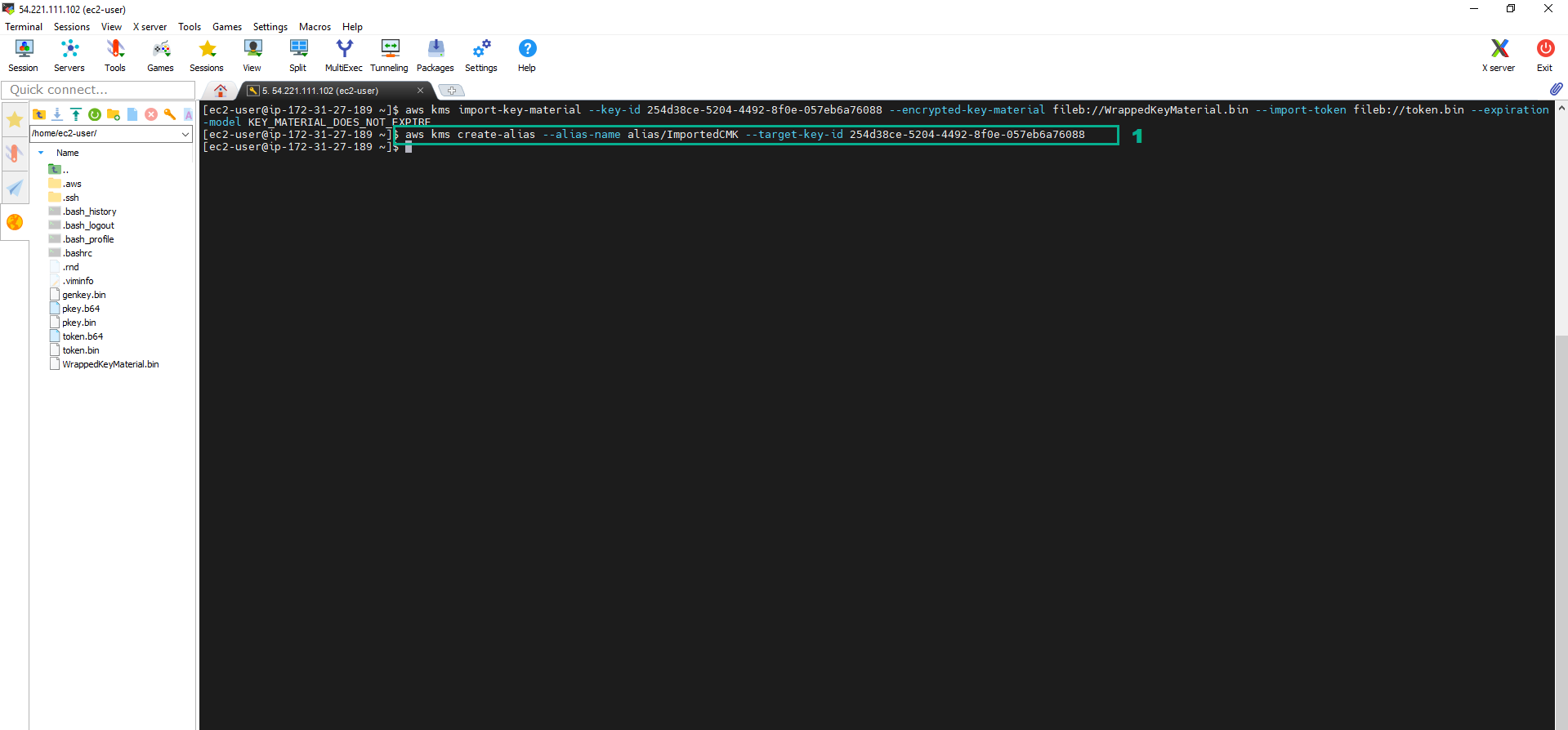
aws kms import-key-material --key-id <key ID of your External CMK> --encrypted-key-material fileb://WrappedKeyMaterial.bin --import-token fileb://token.bin --expiration-model KEY_MATERIAL_EXPIRES --valid-to 2022-06-02T12:00:00-08:00
To import, we will use the aws kms import-key-material command, We will need the import token we have in the token.bin file and the wrapped encrypted key material we have just stored in file WrappedKeyMaterial.bin.
On the expiration date, AWS KMS will delete the key material and the CMK is not longer there for being used. You can always set the expiration model to KEY_MATERIAL_DOES_NOT_EXPIRE instead of KEY_MATERIAL_EXPIRES, if you don’t want the CMK to expire
We need to configure the expiration date for –expiration-model parameter to be able to monitor in CloudWatch (Section 6)
 2. Create the Alias for the CMK we have imported
2. Create the Alias for the CMK we have imported
- Execute the command:
aws kms create-alias --alias-name alias/ImportedCMK --target-key-id <key ID of your External CMK>
 3. To list all of the CMK, execute the command
3. To list all of the CMK, execute the command aws kms list-aliases
The JSON output will display the keys we have created and its alias, along with the aws service CMKs created by default for some of the services.
